Internet Outage: massive DNS DDoS attack hits the world
Early Friday morning, US citizens awoke to large-scale internet outage via a massive DNS DDoS (Distributed Denial of Service) attack on DyN, a company that provides DNS for a number of popular websites. Subsequently, this resulted in the temporary take-down of several popular websites on the east coast. According to The Hacker news, those websites included Twitter, Etsy, Github, Soundcloud, Spotify, Heroku, Pagerduty, Shopify, Intercom, and Netflix.
If you were to visit any of the above sites early this morning, you would have been greeted with a “could not connect” error. No, it’s not just you. Much of the east coast was experiencing those problems this morning.
“This attack is mainly impacting US East and is impacting Managed DNS customer in this region,” DYN wrote at 8:45am EST. “Our Engineers are continuing to work on mitigating this issue.”
DNS servers convert the domain names of websites into computer-digits or IP addresses, like 8.8.8.8 — Google’s DNS. But with a large DNS company like Dyn under attack, the system doesn’t work to translate IP addresses into domain names like www.twitter.com or www.netflix.com. Essentially, without DNS lookup to decipher those string of numbers the internet doesn’t work. There are 13 root DNS servers. If all were attacked, it could potentially bring the Internet to a complete standstill.
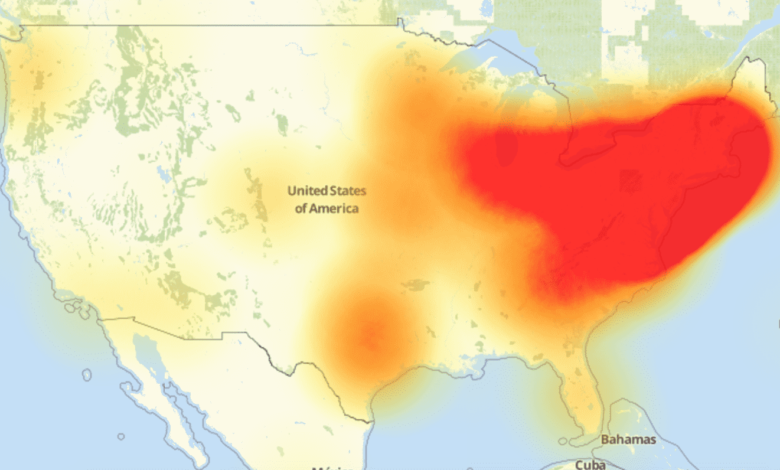
The attack appears to have started around 7 a.m. EST, affecting a huge chunk of the east coast and some parts of the midwest. Level3, which monitors internet activity, revealed the extent of the outage.
This issue has since been rectified, and the websites that were affected seem to be resolving the IP address and working again as of 9 a.m. EST.
“Starting at 11:10 UTC on October 21th-Friday 2016 we began monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure. Some customers may experience increased DNS query latency and delayed zone propagation during this time.” DYN wrote.
So far, no single person or group has taken responsibility for the attack. However, a discussion in a private conversation from a certain hacker a few months back, who was working on what he called “the world’s largest DNS DDoS cannon,” comes to mind. That individual came to me and said that they would be attacking Twitter and avenging Twitter’s alleged shadow-banning of my Twitter account An0nKn0wledge.
It seems logical that this individual or individuals may have possibly been behind the attack, and that this may have just been a test of their power.
We’ll keep you updated on this developing story as more information becomes available.



